5 Physical Views – Stages and Descriptions
Stage 1 – Initial Discovery – Build list of Sites / folder locations to examine. (Tool 1 – Step 1)
Input: File-server mount points.
Process: Crawl the network and build a list of all sub-folders.
Output: List of folder locations.
Stage 2 – Initial Discovery – Examine folders building list of suspects. (Tool 1 – Step 2)
Input: List of folders separated by server and/or mount point.
Process: Search supplied folders for MS Access databases files (all versions).
Output: List of MS Access database files to include new markers of: location, filename, size and date/time last updated.
Notes: These markers are used to help determine the level of risk to the organization.
Stage 3 – Initial Discovery – Re-examine subset of suspect files. (Tool 1 – Step 3)
Input: List of files from Stage 2 minus any files deemed not important to organization, e.g., files which haven’t been opened in a long time or are very small in size.
Process 1 (Tool 1 – Step 3):
Re-examine each suspect file and determine its MS Access version. Version is a key to understanding the risk to the organization because generally, the older the version the less likely the MS Access database application can be easily upgraded to the latest version of MS Access and regain support.
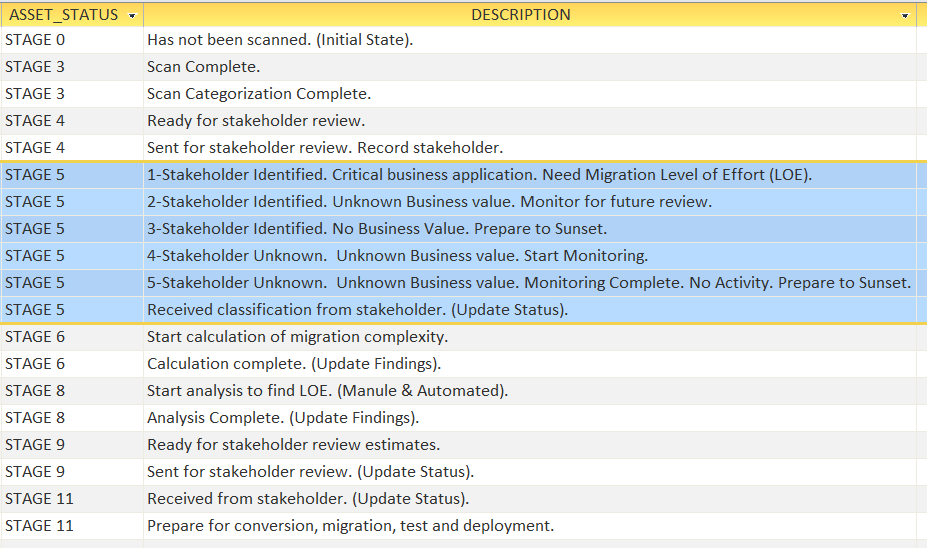
Asset Status = Scan Complete.
Process 2:
Consolidate and conform all stage 3 discovery files into a central repository.
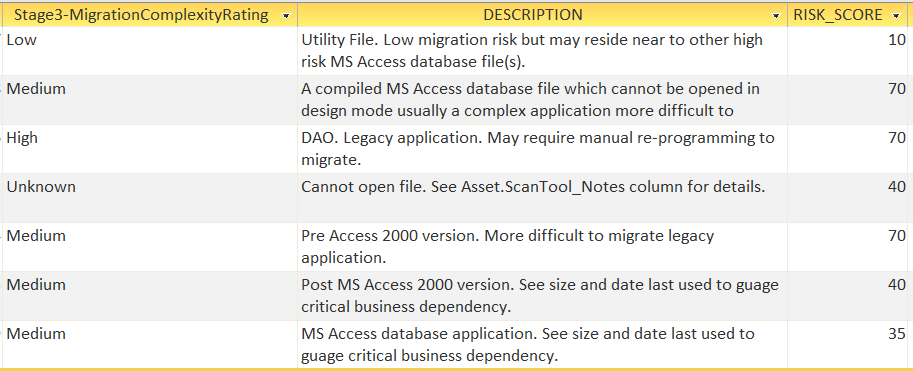
System will calculate the Stage 3 – Migration Complexity Rating:
Asset Status = ‘Scan Categorization Complete’.
FUTURE: Add scores for business value (date last updated, size, location?).
Output: Suspect list from Stage 2 with additional marker of MS Access version. To include only those files identified by client IT as containing high-risk attributes, such as large database files, recently updated and Pre-MS Access 2007 (Microsoft discontinued support, difficult migration path).
Notes: Stage 3 requires considerably more time per file when compared with Stage 2 processing. It is therefore important upon entry of each Stage to pare down the Stage’s input file list to only true suspect files.
Another note to keep in mind, sometimes MS Access databases contain legacy information vital for compliance and may not have been accessed in months or years. These databases are often operated in read-only mode used to lookup old information from sunset systems replaced years ago but their data kept available for research. In this case, last updated may be less important than size of file.
Stage 4 – Initial Stakeholder Interview – Determine risk to business operations.
Given the above findings, present to stakeholders to verify Stage 3 suspects before proceeding to Stage 6 processing.
Consider two lists;
a) Highly probably risk – list all suspects by date/time last modified, size, version and location.
b) List all files by size – to insure not to miss any legacy read-only compliance reporting database applications.
Consider tracking by path and filename and who’s been identified as the key stakeholder.
Stakeholders should be asked to be given a copy of this document so they know how the application files were found and what are the options going forward.
IT/Help4Access will calculate the asset’s risk category.
Stage 5 – Initial Stakeholder Review
Input: Excel spreadsheet listing assets with row for filtering.
Processing: Stakeholders will need to categorize their assets into one of five categories:
Output: Stakeholders will return classified assets to IT/Help4Access.